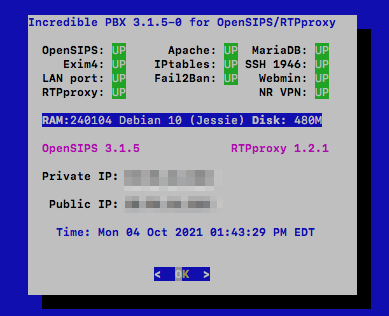
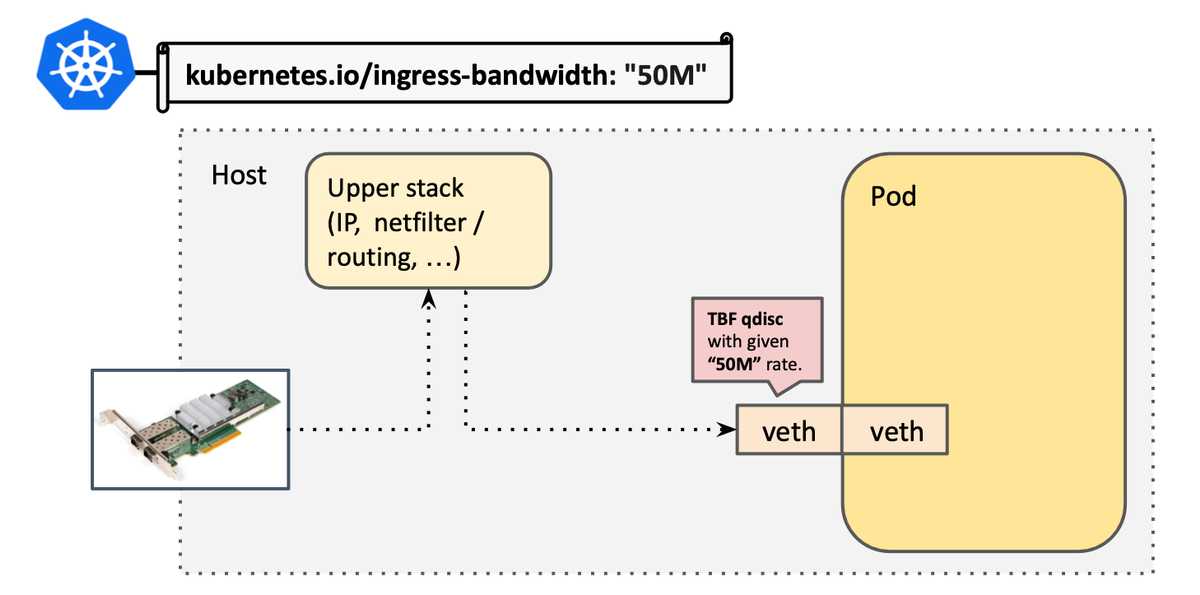
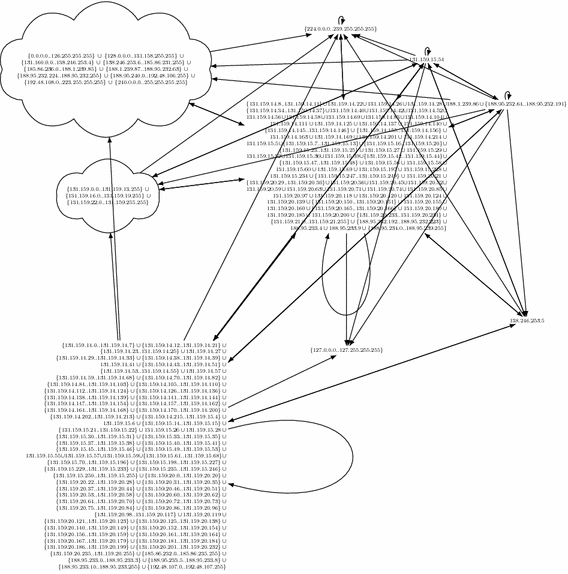
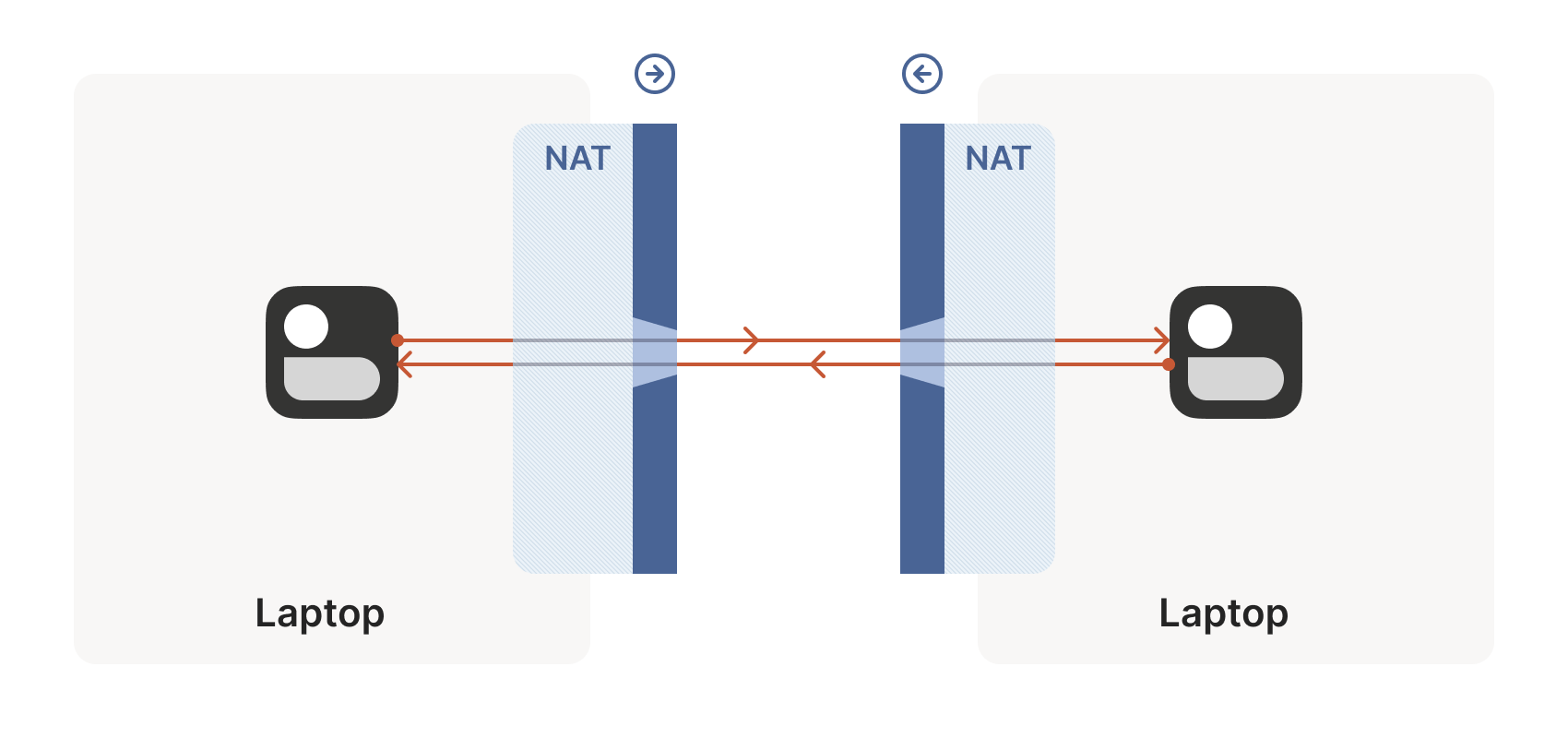
Using systemd-nspawn containers with publicly routable ips (IPv6 and IPv4) via bridged mode for high density testing whilst balancing tenant isolation

PDF) An Anomaly Detection and Network Filtering System for Linux Based on Kohonen Maps and Variable-order Markov Chains

The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory | Wiley